Have you ever considered how secure your internet connection is at home?
In an era where our digital lives are intertwined with our physical reality, securing our online access is not just optional… it’s essential.
A good friend of mine did not have her home protected in the most basic way to protect her online access, as discussed previously.
For beginners, when I asked her if she had a router, her first question was…
Table of Contents
What is a Router
Modem vs. Router: Security Implications
What is a VPN?
The Essential Role of VPNs
7 Essential Steps to Secure Your Home Network
Conclusion
What is a Router?

A router is essentially the heart of your home or office network.
It’s a device that allows you to connect multiple devices—like your smartphone, laptop, tablet, and smart home gadgets—to the internet …and, even to each other… if you wanted to.
Think of it as a digital traffic director.
When you want to send an email, watch a streaming video, or browse a website, the router receives your request and directs it to the internet.
Similarly, when information is sent back from the internet to you, the router makes sure it gets to the right device on your network.
Routers perform several key functions to manage this digital traffic
Routers…
1.) Connect to your modem: The modem is the gateway to the internet provided by your internet service provider (ISP).
The router connects to the modem and receives internet data.
2.) Create a local network: This allows your devices to communicate with each other wirelessly (via Wi-Fi) or through wired connections (using Ethernet cables).
This network is what enables you to send documents to your printer, stream a movie to your TV, or play online games without using the internet.
3.) Assign IP addresses: Your router assigns a unique IP address to each device on your network.
This IP address is like a mailing address for data… it ensures that the information sent from the internet reaches the correct device on your network.
4.) Provide security: Routers have built-in security features, such as firewalls and password protection, to help protect your network and devices from unauthorized access and cyber threats.
Thankfully, I learned THIS bonus back in Windows 3.1 days.
5.) Manage traffic: And now routers even prioritize traffic to ensure that more urgent data, like a video call, gets bandwidth preference over less time-sensitive data, like a software update download.
This helps keep your online activities running smoothly.
To sum this up… a router is your gateway to accessing the internet and allows multiple devices to connect, communicate, and share data both with each other and with the online world.
It’s a crucial piece of technology for anyone looking to get online, offering both connectivity and protection for your digital activities.
NOTE: This is why is it vital that you do NOT allow just anyone to use your internet connection as their device COULD compromise your entire network.
When I explained this to Martha, she said that she had her TV connected through Wi-Fi but did NOT have a router, only a modem.
Ahhh yes, many modern modems indeed come with built-in Wi-Fi capabilities, essentially combining a modem and a router into a single device.
Modem vs. Router: Security Implications

These are often billed as ‘gateway devices’, and most definitely not my favourite watch-dog for my internet connection.
They’re too much like an all-in-one kitchen appliance versus separate specialized tools.
Though a modem-router combo offers convenience by combining two devices into one, a separate modem and router can provide stronger performance …and… security… much like specialized kitchen tools can achieve better results for specific tasks.
Here’s why I say this…
Simplifying one’s internet access if making it simpler for potential hackers too.
So, though one device might save you space on a shelf, it may not provide you with the best type of protection.
Plus, separating your router-modem devices may offer more flexibility for upgrades.
If you only need to upgrade your router for better Wi-Fi coverage or features, having a separate router makes this easier.
And, in some cases, standalone routers may offer better performance, more advanced features, or a greater range than the router portion of a combo device.
NOTE: The security of your home network in relation to having a combined modem-router unit versus separate devices isn’t inherently about the devices themselves but how they are configured and updated.
However, there are a few nuances that could influence security considerations:
1.) Firmware Updates: The basic, built-in software that controls how your router or modem operates.
Separate devices may receive updates more frequently or more promptly than combined units.
Manufacturers of standalone routers often push out firmware updates to address security vulnerabilities more quickly, as their focus is solely on networking devices.
On the other hand, modem-router combos provided by ISPs might not receive updates as regularly, potentially leaving known vulnerabilities unpatched for longer.
2.) Security Features and Customizations: Standalone routers often offer more advanced security features and customizable options compared to the router portion of a combo unit.
This could include better firewalls, intrusion detection systems, and the ability to install third-party firmware like DD-WRT or OpenWRT, which can offer enhanced security features (speak to your chosen ‘computer doctor’ about these, first, before deciding).
Users who are keen on maximizing their network security might find standalone routers offer more tools to do so.
3.) Device Vulnerabilities: The idea for separating the modem and router provides an additional layer of security stems from the concept of network segmentation.
If a hacker were to compromise the router in a combo unit, they might more easily gain access to the modem functionality, potentially allowing them to tamper with your internet connection.
With separate devices, an additional step is required to compromise both the router and the modem.
However, this scenario largely depends on the specific vulnerabilities of the devices and the network configuration.
[PERSONAL OPINION: in today’s world of ISPs to choose from, I have to wonder if any of them truly focus on YOUR internet security like they should/could be.]
4.) ISP Access: ISP-provided modem-router combos are sometimes managed remotely by the ISP for updates and troubleshooting.
This can be convenient but also means there’s a potential vector for attacks if the ISP’s systems are compromised.
Standalone routers typically give the user full control, reducing the risk of unauthorized access via the ISP.
In practice, the most significant factors in securing your home network are to ensure your devices are regularly updated, change default passwords, use strong encryption for Wi-Fi, and disable any features you don’t use that could open security holes.
Whether you choose a combined unit or separate devices, staying proactive about security really is key.
Now…
More recently there has been a new NEED for yet another layer of protection from online spies, and that is a Virtual Private Network (VPN).
What is a VPN?
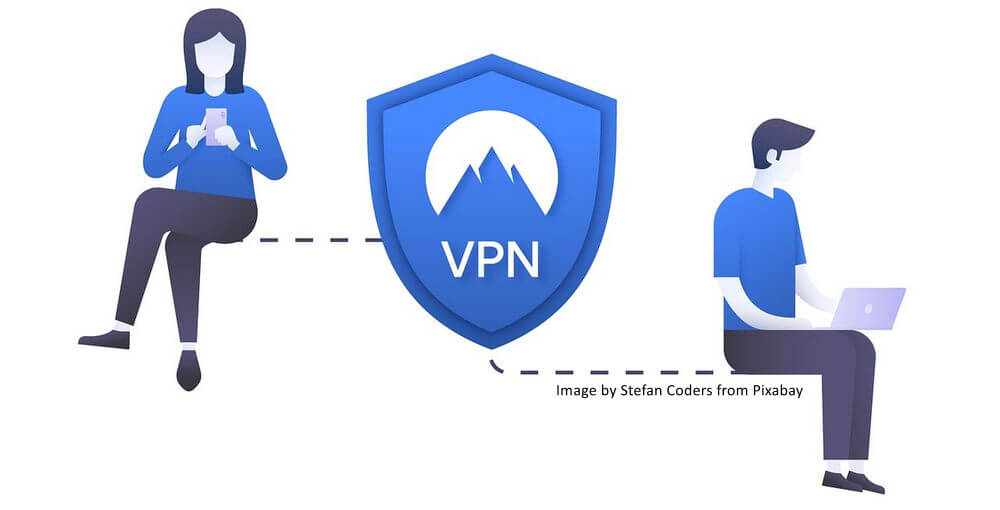
A VPN is a protected network connection that encrypts your data and hides your IP address when you use the internet.
OR better still…
Using a VPN is like sending your internet traffic through a private tunnel, hidden from the outside view.
Adding a quality VPN service to your internet access can significantly enhance your online security, privacy, and anonymity.
However, the extent of the safety and privacy you gain depends on several factors, including the VPN provider’s policies, the strength of the encryption used, and the specific threats you’re concerned about.

The Essential Role of VPNs
Here’s how a VPN contributes to your online security and privacy, along with some considerations:
1.) Encryption: A VPN encrypts your internet traffic, making it difficult for anyone on the same network (such as public Wi-Fi) to intercept and read your data.
NOTE: A good example would be your cell phone when you’re away from home.
In other words, it scrambles your data so only the intended recipient can unscramble and read it.
This encryption protects your online activities from eavesdroppers and is especially beneficial when using unsecured or public Wi-Fi networks.
2.) Anonymizing Your IP Address: VPNs hide your real IP address (much like the address for your home, your computer has an address known as an IP address showing EXACTLY where your computer is located), making it more difficult for websites, advertisers, and potential attackers (yes, even Google!) to track your online activities.
By connecting to a VPN server, your online actions appear to come from the VPN’s IP address, not your own, enhancing your anonymity on the internet.
3.) Bypassing Geo-Restrictions: VPNs can make it seem as though you’re accessing the internet from a different location, allowing you to bypass geo-restrictions and censorship.
This is much like using a post office box in another city to receive mail, which doesn’t reveal your actual location.
This is particularly useful for accessing content or services not available in your country.
Example might be a website developer with clients in another country, they need to know how their client’s website appears in search results for their client’s country.
4.) Mitigating Risk of Man-in-the-Middle Attacks: Much like Martha’s having a hacker secretly listening to her phone conversations now that her landline is using the internet.
By encrypting your data, a VPN reduces the risk of man-in-the-middle (MitM) attacks, where an attacker intercepts the communication between you and another server to steal or manipulate your data.
5.) Secure Data Transmission: If you’re transmitting sensitive information (example: using financial services, sending confidential emails), a VPN adds an extra layer of security, ensuring that your data is encrypted and more difficult for unauthorized parties to access.
Considerations:
- VPN Provider Trust: Your VPN provider will have access to your internet traffic, so it’s crucial to choose a reputable provider that has a strict no-logs policy and is transparent about their operations.
- VPN Security Protocols: The security of a VPN connection depends on the protocols it uses.
Protocols like OpenVPN and WireGuard are known for providing strong encryption and security. - Potential Limitations: While a VPN provides increased security and privacy, it’s not a cure-all.
You still need to be cautious about malware, phishing attacks, and ensuring your devices are secure and up-to-date.Example: do NOT respond to pop-up prompts that appear to be from a reputable online service requiring you to change your password by providing your password first and then the new one.
Limitations:
- VPN Does Not Protect Against All Threats: A VPN won’t protect you from phishing attacks, viruses, or malware (READ AND HEED!).
It’s essential to use a VPN in conjunction with other security measures, such as a good antivirus program and safe browsing practices. - Dependence on VPN Provider Security: The security and privacy benefits of a VPN are contingent upon the integrity and policies of the VPN provider.
Some free or low-quality VPN services might log your data or have insufficient security, negating the benefits.
It’s much like the old adage: ‘you get what you pay for’.
Securing your home network might seem daunting, but these seven simple steps can significantly enhance your digital safety.

7 Essential Steps to Secure Your Home Network
- Update Your Devices: Regularly check for and install firmware updates on your router and any other network devices.
This could save you a major outage right when you need your internet access most. - Change Default Passwords: Replace any default passwords with strong, unique passwords of your own.
Using over 12 random characters with a mixture of caps, lower case, numerical, and punctuation is highly recommended.
Hackers only go after easy passwords. - Enable Wi-Fi Encryption: Ensure your Wi-Fi is protected with WPA3 encryption.
If not available, use WPA2.
For this I recommend you reach out to your highly-trusted computer doctor.
Mine even offers remote access maintenance. - Research VPN providers: Look for one with strong encryption and no-logs policies.Install and use a VPN for all online activities.
There are a range of excellent VPN providers.
Ask a friend which one they use and then DO YOUR RESEARCHING.
Some people skip this step and then wish they had of checked FIRST after it’s too late. - Avoid over-synchronizing devices: All device that leaves access your internet needs its very own email account. Never use the same email address for every device.
- Keep your online accounts separated: Keeping these separated increases your online security for your online accounts.
Example: never join your Google account to access Canva, Facebook, etc.
Setup different individual access exclusive to each online account to keep them separated.
This will make it less likely that all your accounts will be hacked at once. - Do not get phished in: Businesses like Google will NOT send your mobile device a warning that you better change your password right now or your device will be locked.
If in doubt… take your device in to your supplier/repair person or at least call them (using your landline) for advice.
It’s much easier to delay responding then to pay the hefty price that Martha paid when she went through 4 cell phones, repeatedly getting phished in by those clever hackers.
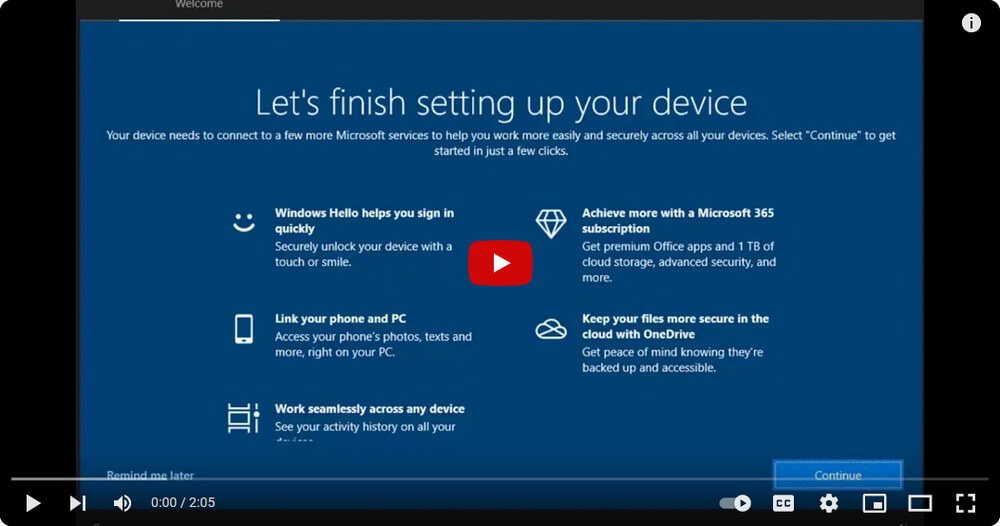
The following is a BONUS tip for those seeing the following annoying screen when starting up your computer – How to STOP this message.
Simply click the image and the YouTube video will open in a new tab, so that you can easily return to finish reading this article.
Conclusion
It’s time to Fortify Your Digital Domain
In our journey through the intricacies of internet security, we’ve navigated a landscape rich with both threats and defenses.
The digital realm, much like the physical world, requires diligence, awareness, and proactive measures to ensure your sanctuaries remain unbreakable.
Your home network is the gateway to your personal and professional worlds…
It deserves vigilant protection.
By embracing practices like regular updates, separating your modem and router, and employing a VPN, you fortify this gateway against unwelcome intrusions.
Remember, securing your online presence is a continuous journey, evolving as technology does.
As technology evolves, so too do the tactics of those with malicious intent.
Stay informed, stay cautious, and regularly revisit your security measures to adapt to new challenges.
Take Action Today:
Don’t wait for a breach to remind you of the importance of your digital security.
Whether it’s updating your router’s firmware, changing default passwords, or setting up a VPN, each action is a step towards a more secure footprint.
In safeguarding our digital domains, we not only protect our personal information but also contribute to a safer, more secure internet for all.
The real sadness in Martha’s story is her ongoing fear and retreat from online engagement.
This is a stark reminder of the deep impact digital insecurity can have on our lives, as well I can understand, having had my offline life security threatened in years past.
But it’s never too late to start making changes.
Small, manageable steps can significantly enhance your security and peace of mind.
Which of these steps will you take today to protect your digital world?
Share with friends and family… let’s secure our digital futures together.
Other’s Story
I Fell For A Scam — Here’s What I Leaned From It
My friend’s scammers may have now been caught! 10 arrested in SIM swap fraud investigation: Toronto police 01 Aug 2024
Credit for Header: Image by DALL-E and padlock graphic Image by Akhil J from Pixabay